This paper is available on arxiv under CC 4.0 license.
Authors:
(1) Ayei E. Ibor, Trustworthy Digital Infrastructure for Identity Systems, The Alan Turing Institute, United Kingdom;
(2) Mark Hooper, Trustworthy Digital Infrastructure for Identity Systems, The Alan Turing Institute, United Kingdom;
(3) Carsten Maple, Trustworthy Digital Infrastructure for Identity Systems, The Alan Turing Institute, United Kingdom;
(4) Gregory Epiphaniou, WMG, University of Warwick, United Kingdom.
Table of Links
Conclusion and Future Work & References
4. Methodology
To underscore the importance of interoperability in developing countries, an investigation and comparison of current interoperability solutions in the identity ecosystem was performed. This investigation identified the current limitations of existing solutions and provided the basis for our findings, which are relevant to achieving interoperability for foundational identity systems in developing nations. As a guide, we have presented an approach for the investigation of requirements in Figure 2.
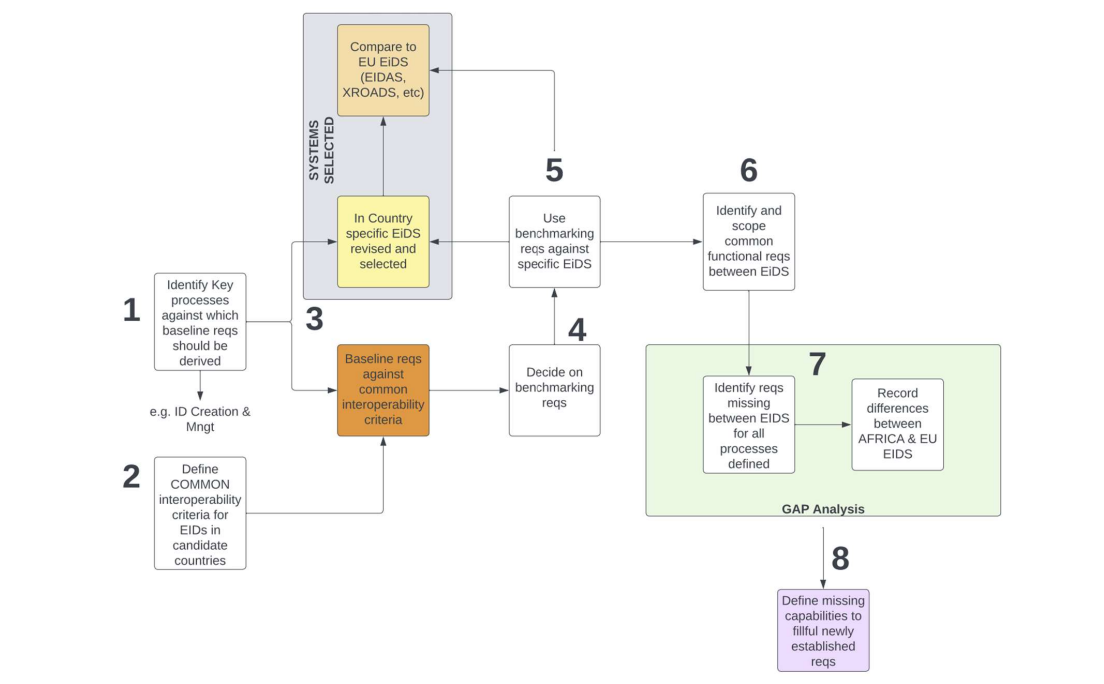
The approach in Figure 2 is an easy stepwise guide. The steps include:
i) Identify key processes against which baseline requirements should be derived: these processes are already identified in this work.
ii) Define common interoperability criteria for eID schemes in candidate countries: this is an important step that must be fulfilled based on the identified key processes of step 1.
iii) Baseline requirements against common interoperability criteria, select and compare country-specific eID schemes with current interoperability solutions such as eIDAS and X-Road: this step allows for the identification of common functionalities among eID schemes relative to defined common interoperability criteria.
iv) Decide on the benchmarking requirements: it is important to decide on the benchmarking requirements to adequately scope the functional requirements useful for a fully functional interoperable system.
v) Use benchmarking requirements against specific eID schemes: using benchmarking requirements against specific eID schemes is useful for identifying missing requirements and functionalities.
vi) Identify and scope common functional requirements between eID schemes: this is a significant step that ensures that all requirements for interoperability are adequately captured.
vii) Perform requirements gap analysis by identifying missing requirements between eID schemes for all processes defined and recording the differences between eID schemes: the missing requirements must be identified in this step concerning the processes defined in step 1. All significant differences between eID schemes must be recorded (e.g. in Africa and Europe).
viii) Define missing capabilities to fulfil newly established requirements: it may be necessary to define missing capabilities in the investigated eID schemes that are relevant to the identified requirements to realise an interoperable identity system. However, this may not be the case where such eID schemes fulfil most of the baseline requirements for interoperability.
4.1 Current Interoperability Solutions
For the creation of effective, long-lasting, and usable identity ecosystems, interoperability is essential. Two major interoperability solutions in the identity ecosystem are discussed in this research. These include the Estonian X-Road and the electronic identification and trust services (eIDAS) of the European Union. X-Road is a data exchange layer solution that implements the interoperability of information systems. It allows organisations to exchange data through a secure channel over the Internet. This solution is centrally managed but supports a distributed exchange layer that provides a standardised and secure channel for producing and consuming services (X-Road, 2023a, 2023b).
X-Road enhances the confidentiality, integrity, and interoperability between organisations that rely on it for data exchange (Bakhtina et al., 2022; Saputro et al., 2020). Jointly implemented by Estonia and Finland, it has been adopted by several countries and organisations (Saputro et al., 2020). As stated in Solvak et al. (2019), X-Road establishes online connections between service providers and data registries (such as the Population Register, Health Insurance Register, etc.). The citizens who use the X-Road system only give their information to the government once, and the public authority then stores and exchanges the information among itself via the X-Road system (Bhattarai et al., 2019).
By signing the messages with the X-Road member's signature key and using a mutually authorised Transport Layer Security (TLS) channel, security servers guarantee the integrity and secrecy of the exchanged messages. By recording the exchanged messages and routinely timestamping the message logs, the signed communications' long-term evidential value is protected. To obtain information on the validity of certificates and timestamp-signed messages, the security servers communicate with trust services. In terms of message exchange, the trust service calls are asynchronous (X-Road, 2023c, 2023d).
To exchange messages between a service client and a service provider, three protocols are used. These include X-Road message protocol, X-Road message transport protocol, and OCSP response retrieval protocol (X-Road, 2020). When an interested party such as an organisation joins an X-Road ecosystem, certificates issued by a reputable Certification Authority (CA) are used to verify the identification of each organization and security server. Each security server serves as the technical entry point that manages access control on the organisation level during the data exchange process between registered X-Road members (European Commission, 2023a; X-Road, 2023a). The combination of timestamping and a digital signature ensures that data delivered via X-Road cannot be disputed.
On the other hand, eIDAS is a European Union’s framework to ensure that electronic transactions between businesses, citizens, and public agencies are safer and more efficient, regardless of the European country they take place in. It is established by a European Regulation that was implemented in 2014. By introducing a common framework for eID and trust services, the eIDAS regulation makes it easier to supply business services across the EU. It encourages interoperability across the 28 EU nations, making certain that nations mutually recognise each other's electronic identities and trust services across borders (Mocanu et al., 2019).
The goal of electronic identification is to completely transform how customers engage with online services. The Member States of the EU may choose to identify citizens electronically. A small number of Member States have created national programs to provide their citizens with electronic identity (eID), with greatly diverse architectures (Lips, Bharosa and Draheim, 2020). National systems, therefore, vary not only in the volume of citizen data they process but also in the degree of data protection they provide to this data.
As claimed by Cuijpers and Schroers (2014) and Hölbl, Kežmah and Kompara (2023), businesses and customers can more easily access services or conduct commercial transactions by using electronic identity, or eID, to identify who they are (identification process) and demonstrate that they are who they claim to be (authentication process). Similarly, the regulation stipulates that it will be necessary for all EU nations to accept notified eID systems from other nations by September 2018. When conducting electronic transactions, especially those between firms and clients who are based in another EU country, trust services attempt to improve the trust of EU residents and enterprises (Sharif et al., 2022).
The trust services in eIDAS as discussed in ANSSI (2023) and European Commission (2023b) include Electronic Signature (eSignature), Electronic Seal (eSeal), Electronic Timestamp (eTimestamp), Website Authentication Certificates (WACs), and Electronic Registered Delivery Service (eDelivery). eIDAS has been exploited by both the public and private sectors in the EU. Some of the sectors that have benefited from the regulation include the financial services, online retail, transport, and professional services sectors. One of the largest potential beneficiaries of eID and trust services is the financial services industry due to the possibility of enormous commercial opportunities and enhanced cross-border services (Cuijpers and Schroers, 2014; European Commission, 2023b). To meet rising client demand for online services as well as stricter compliance requirements, the identification, authentication, and safeguarding of transactions in the financial services sector are becoming increasingly digitised.
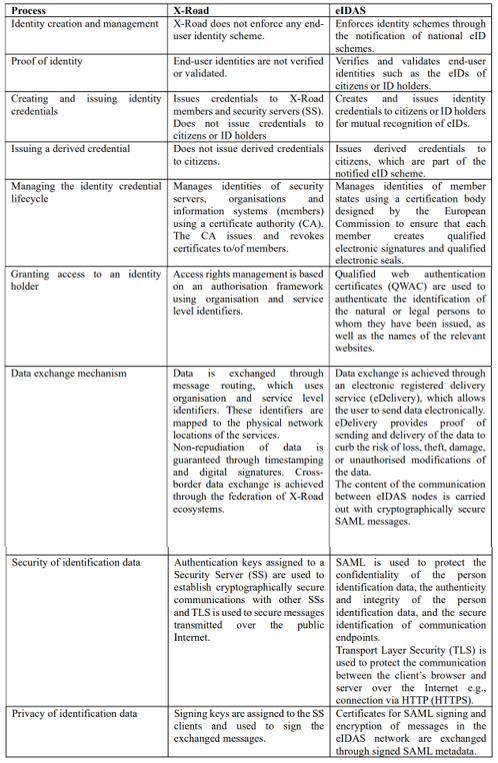
4.2 Comparison of X-Road and eIDAS as Interoperability Solutions
The comparison of X-Road and eIDAS is given in Figure 3. This comparison is performed based on identity creation and management, proof of identity, creating and issuing identity credentials, issuing a derived credential, managing the identity credential lifecycle, granting access to an identity holder, data exchange mechanism, security of identification data, and privacy of identification data.
This paper is available on Arxiv under CC 4.0 license.

